This in-depth article explores how passkey authentication works, emphasizing its use of cryptographic keys and biometric data to replace traditional passwords. It examines the enhanced security, improved user experience, and seamless integration across platforms for both technical and non-technical users, offering a comprehensive perspective suitable for diverse audiences.
1. Introduction
The rapid evolution of digital security challenges has pushed organizations and developers to reconsider traditional authentication methods. With the increasing prevalence of cyber threats and the cumbersome nature of password management, passkey authentication has emerged as a revolutionary alternative. Passkeys leverage public-key cryptography and biometric data, aiming to provide a seamless, secure, and user-friendly solution across multiple devices and platforms.
This article offers an in-depth analysis of passkey authentication mechanisms. It examines how passkeys are created, how they operate during the registration and authentication processes, and how they manage to replace traditional password-based methods. Additionally, we will discuss the enhanced security afforded by cryptographic keys and biometrics, the convenience of cross-device authentication, and best practices recommended for successful implementation. Throughout the article, supporting data and insights from current research and user studies are integrated to provide a comprehensive perspective for technical and non-technical audiences alike.
2. Technology Behind Passkey Authentication
Passkey authentication is fundamentally built on the principles of public-key cryptography (PKI). In this system, each passkey consists of a unique pair: a public key and a private key. The private key is securely stored on the user’s device, while the public key is shared with the application or website for authentication purposes. This design ensures that if one component is compromised, the other remains secure, reducing the potential damage from security breaches.
2.1 Cryptographic Foundations
- Public-Key Cryptography (PKI):
Passkeys use asymmetric cryptography where the key pair is generated during the registration process. The private key never leaves the secure storage of the device, and the public key is transmitted for registration or verification purposes. - Biometric Integration:
To further enhance security, modern devices incorporate biometric sensors such as fingerprint readers, facial recognition, or even PIN-based methods. This ensures that only the rightful owner of the device can authorize the usage of the passkey. - Phishing Resistance:
One of the major advantages of passkeys is their resistance to phishing. Because each passkey is created for a specific website or application and never shared across multiple platforms, the risk of accidental credential leakage is significantly minimized.
2.2 Underlying Protocols and Standards
Passkeys comply with modern authentication protocols including FIDO2 and WebAuthN. These standards were designed to facilitate secure, passwordless authentication while ensuring that websites can verify the authenticity of the devices attempting to sign in. In certain scenarios, such as in enterprise environments managed by Entra ID, passkeys are integrated with additional security measures such as the allowCredentials parameter, which restricts which devices can be used for authentication based on security policies.
3. Registration Process for Passkeys
The registration process is the first critical step in using passkeys. It involves generating a secure key pair and associating the public key with the user’s account on an application or website. This process can be visualized in the following flow diagram.
3.1 Registration Flow
When a user opts to create a passkey:
- The user navigates to the registration page of a website that supports passkey authentication.
- The browser sends a nonce (a unique, one-time code) to the client device, which forwards it to the authenticator (such as the Microsoft Authenticator App).
- The authenticator generates a new key pair: a public key and a private key. The private key is stored securely on the device, while the public key is sent back, along with the signed nonce, to the website for registration.
- The website stores the public key and associates it with the user’s account, thereby completing the registration process.
Below is a Mermaid diagram illustrating this registration process:
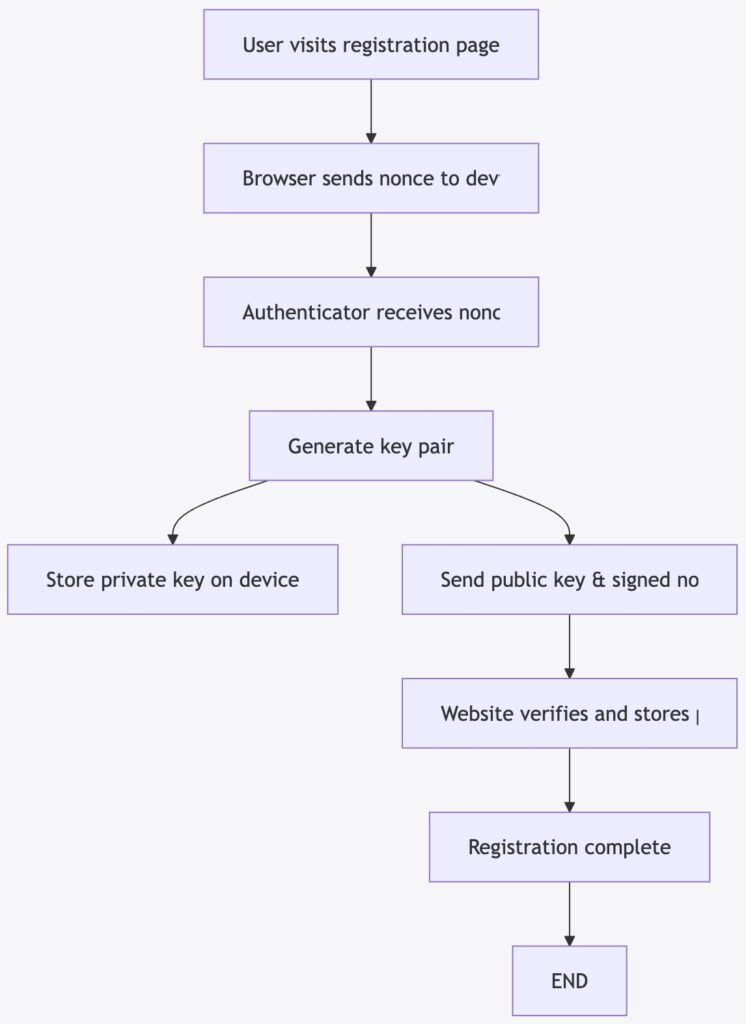
Figure 1: Registration Flow for Passkeys
3.2 Key Considerations During Registration
- Seamless User Experience:
The registration process is designed to be seamless and quick, often requiring only a few seconds to complete compared to the traditional method of creating and remembering strong passwords. - Security Assurance:
The cryptographic process ensures that even if data transmitted to the server is intercepted, the private key remains secure on the user’s device. - Fallback Options:
In scenarios where passkey registration fails or is not supported (for instance, on older devices), organizations provide alternative authentication methods, such as QR code-based sign-in flows or traditional passwords.
4. Cross-Device and Cross-Platform Functionality
One of the standout features of passkey authentication is its ability to facilitate cross-device sign-in. This functionality allows users to authenticate themselves on devices that do not store their passkey directly by using a secondary device that does. This greatly enhances convenience and further reinforces security.
4.1 Cross-Device Sign-In Mechanism
In a typical cross-device scenario, a user who has registered a passkey on a smartphone can use that smart device to authenticate on a desktop or laptop that might not have the passkey available locally. The process involves the following steps:
- The user initiates the sign-in process on the primary device (e.g., a laptop).
- The primary device presents a QR code or similar prompt.
- The user then uses a secondary device (e.g., a smartphone) where the passkey is stored to scan the code and approve the sign-in request.
- Once authenticated, the primary device can access the account or application securely.
4.2 Cross-Platform Integration
Passkeys are not limited to a single ecosystem. They are supported by major platforms such as Microsoft Authenticator, Google Password Manager, and Apple’s iCloud Keychain, providing a unified approach to authentication across different operating systems and browsers. This interoperability ensures that users can transition seamlessly between environments without the need for multiple credentials.
4.3 Visual Representation: Cross-Device Sign-In
Below is a table that summarizes the key features and communication methods used in cross-device passkey authentication.
| Feature Category | Description | Example/Methodology |
|---|---|---|
| Device Role | Primary device (without passkey) and secondary device (with passkey) | Laptop and smartphone |
| Communication Method | QR code scanning, NFC, Bluetooth, or USB | QR code prompt; CTAP protocol |
| Security Protocol | Use of signed nonce and verification via public key cryptography | WebAuthN and FIDO2 standards |
| Fallback and Redundancy | Alternative sign-in methods if passkey-based authentication fails | Traditional password or OTP |
Table 1: Key Features of Cross-Device Passkey Authentication
5. Security Benefits and User Experience Enhancements
The transition from traditional passwords to passkeys marks a significant improvement in both security and user convenience. This section details the benefits that passkeys offer over passwords.
5.1 Enhanced Security
- Phishing Resistance:
Unlike passwords that might be intercepted through phishing techniques, passkeys are strictly domain-specific. They only function for the website or application they were registered with, preventing attackers from reusing stolen credentials on fraudulent sites. - Asymmetric Key Storage:
The storage of only the public key on server infrastructure reduces potential damage if a server is breached. Attackers are left with minimal exploitable information, as the private key remains secured on the user’s device. - Two-Factor-Like Functionality:
The inherent link between the device (something you have) and the user’s biometric or PIN (something you know or are) creates a robust two-layer security mechanism. This adds an extra barrier against unauthorized access compared to traditional passwords.
5.2 Improved User Experience
- Seamless, Fast Logins:
With passkeys, users can log in in about 3 seconds—a significant improvement over the average 9 seconds with traditional password entry. This speed enhances overall usability significantly. - Reduced Cognitive Load:
Users are relieved from the burden of remembering multiple complex passwords, which minimizes password fatigue and the risk of poor password hygiene. - Streamlined Cross-Device Navigation:
The ability to authenticate using a secondary device means that users can effortlessly switch between personal and public or shared devices, providing a consistent experience regardless of device constraints.
5.3 Visual Comparison: Authentication Methods
The following table compares traditional passwords with modern passkeys based on several criteria such as security, ease of use, and speed.
| Authentication Method | Security Level | Ease of Use | Authentication Speed | Phishing Resistance |
|---|---|---|---|---|
| Traditional Password | Low | Moderate | Slow | Low |
| Password + MFA | Medium | Moderate | Moderate | Medium |
| Passkeys (Passwordless) | High | Very Easy | Fast (≈ 3 sec) | Very High |
Table 2: Comparative Analysis of Authentication Methods
6. Challenges and Potential Drawbacks
While passkey authentication offers significant advantages, it is not without its challenges. A balanced perspective is essential to understanding both the practical benefits and the obstacles that organizations and users might face.
6.1 Compatibility Issues
- Device and Operating System Requirements:
Passkeys are typically available only on modern devices running up-to-date operating systems. Older devices may not support the required biometric sensors or cryptographic protocols, limiting the adoption of passkeys. - Cross-Ecosystem Limitations:
Although major ecosystems like Apple’s iCloud, Google’s services, and Microsoft Authenticator support passkeys, transferring passkeys between different ecosystems (e.g., iOS to Android) can be challenging. The lack of a universal standard for cross-ecosystem synchronization may necessitate fallback methods.
6.2 User Learning Curve
- Initial Familiarity:
For many users, the transition from traditional passwords to passkeys involves understanding new concepts such as biometric authentication and using secondary devices for sign-in. Even though the process is designed for ease of use, the unfamiliarity can initially lead to confusion. - User Expectation Management:
It is crucial for organizations to provide clear instructions and user support during the rollout of passkey-based authentication to ensure that users do not feel overwhelmed by the change.
6.3 Proximity and Connectivity Requirements
- Dependence on Proximity:
Some implementations require physical proximity between devices (using Bluetooth, NFC, or USB). While this adds a layer of security, it may also pose challenges in scenarios where the secondary device is not immediately available or when connectivity issues arise. - Fallback Mechanisms:
In situations where connectivity between devices is lost or the passkey is not accessible, organizations must ensure that secure fallback authentication methods remain in place. This may include traditional passwords or other multi-factor authentication options.
6.4 Cost and Resource Implications
- Initial Investment:
Although passkeys reduce ongoing costs associated with password management and customer support for password recovery, there might be an upfront cost in terms of technology upgrade and training for both users and IT personnel. - Managing Multiple Ecosystems:
Organizations operating across diverse technological ecosystems might face challenges in integrating passkey solutions uniformly, potentially resulting in additional administrative overhead.
7. UX Best Practices and Implementation Considerations
Implementing passkey authentication successfully requires not only an understanding of the technical framework but also a deep commitment to enhancing the user experience. Several best practices have emerged from extensive UX testing and research, ensuring that passkeys are both secure and user-friendly.
7.1 Seamless Onboarding and Registration
- Contextual Prompts:
Users should be prompted to create passkeys at strategic moments, such as during initial account registration or immediately after recovery processes. This proactive approach increases the likelihood that users will adopt passkeys as their primary authentication method. - Clear Communication:
Explaining the benefits of passkeys—such as enhanced security and faster login times—helps users understand why transitioning away from passwords is beneficial. This communication should be integrated into both the user interface and accompanying documentation.
7.2 Accommodating Diverse User Journeys
- Multiple Sign-In Options:
Even if passkeys are available, providing alternative sign-in options (e.g., QR codes, traditional passwords, or email OTP) helps ensure that users are not locked out in case of compatibility or connectivity issues. - User Feedback Channels:
Collecting user feedback during the onboarding process can help identify issues early and facilitate improvements in the authentication flow. Incorporating intuitive error messages and clear recovery options enhances confidence among users.
7.3 Visual and Interaction Design
The design of the authentication interface should prioritize simplicity and clarity. For example, the unobtrusive passkey autofill feature minimizes the need for manual input and streamlines the sign-in process on supported devices.
Below is a Mermaid flowchart illustrating an optimal user journey during sign-in with passkeys:
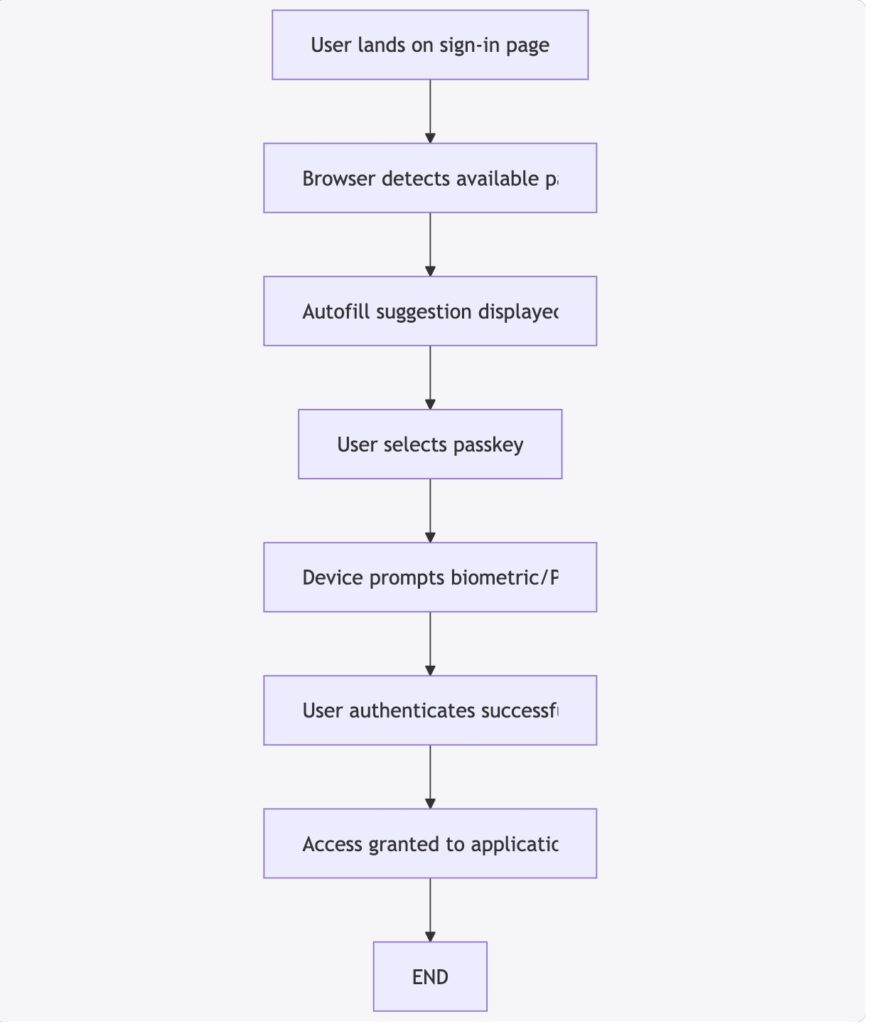
Figure 2: Optimal User Journey for Passkey Sign-In
7.4 Accessibility and Inclusivity
- Device Diversity:
Ensure that passkey solutions are accessible across a broad range of devices and operating systems. Special efforts should be taken to accommodate users who rely on shared or public computers, as well as those lacking modern biometric capabilities. - Educational Resources:
Providing video tutorials, FAQs, and interactive guides can ease the adoption process for users who are unfamiliar with passkey technology. This support is critical for building trust and ensuring a smooth transition from traditional methods.
8. Comparative Analysis: Passkeys vs Traditional Methods
A prudent evaluation of passkeys requires comparing them directly with traditional methods such as passwords and password-plus-multi-factor authentication (MFA) systems. This section offers a detailed comparative analysis based on multiple dimensions.
8.1 Security
- Passwords:
Rely on memorization and can be easily compromised by reuse, brute force attacks, or phishing. The static nature of passwords makes them vulnerable to credential stuffing. - Password + MFA:
Adds an extra layer of authentication but still relies on the inherent weaknesses of passwords. The additional step, while improving security, introduces extra friction for users. - Passkeys:
Use asymmetric cryptography and are inherently resistant to phishing. With biometric integration, they offer a level of security that is far superior to that of traditional methods. Additionally, storing only the public key on servers minimizes the risk of data breaches.
8.2 User Experience
- Passwords:
Require users to remember complex strings and often lead to negative experiences such as password fatigue and inconvenience during recovery processes. - Password + MFA:
Improves security but tends to slow down the authentication process, increasing the overall login time and adding complexity, especially when multiple devices are involved. - Passkeys:
Deliver a quick, seamless login experience that eliminates the need for manual entry. Users benefit from the speed, reduced cognitive load, and simplified cross-device functionality, making the overall experience more enjoyable.
8.3 Deployment and Administration
- Passwords:
Are simple to deploy but demand considerable administrative overhead for resets, recovery, and password management tools. The ongoing support costs can be significant over time. - Passkeys:
Although deployment may require initial investment in infrastructure and training, they tend to lower long-term administrative costs by reducing support calls and the risks associated with password breaches.
8.4 Visual Comparison: Benefits vs. Drawbacks of Passkeys
The table below summarizes the key benefits and potential drawbacks associated with passkey authentication.
| Aspect | Benefits | Drawbacks |
|---|---|---|
| Security | High phishing resistance; secure cryptographic storage | Limited support on older devices; cross-ecosystem transfer challenges |
| User Experience | Fast login; reduced need to remember passwords; seamless cross-device | Initial user learning curve; reliance on device proximity |
| Administration | Lower long-term support costs; reduced risk of breaches | Upfront infrastructure and training investment |
Table 3: Summary of Benefits and Drawbacks of Passkey Authentication
9. Conclusion
Passkey authentication represents a significant turning point in secure digital authentication. By replacing traditional, vulnerable passwords with cryptographic methods and biometric authentication, passkeys offer a robust, phishing-resistant alternative that enhances both security and user experience. Key findings from this in-depth analysis include:
- Enhanced Security:
Passkeys rely on asymmetric cryptography and localized biometric verification, which drastically reduce the risk of phishing and credential theft. - Improved User Experience:
The fast, seamless sign-in process—often taking just a few seconds—reduces user frustration and eliminates the cognitive burden of password management. - Seamless Cross-Device Integration:
The ability to authenticate using a secondary device ensures that users can conveniently access their accounts on multiple platforms and devices without re-enrolling credentials. - Adoption Challenges:
Despite the compelling benefits, challenges such as compatibility with older devices, cross-ecosystem integration, and initial user education need to be addressed to achieve broader adoption. - Practical Best Practices:
Effective deployment of passkeys requires clear user guidance, accessible support resources, and fallback authentication methods to ensure a smooth, inclusive transition to a passwordless future.
Key Takeaways
- Security: Passkeys offer a robust, phishing-resistant mechanism by using public-key cryptography and biometric data.
- User Convenience: Eliminating the need for traditional passwords significantly enhances the user experience while reducing login times.
- Cross-Platform Functionality: Seamless sign-in across devices ensures consistent access and improved security without compromising convenience.
- Implementation: A holistic approach that includes fallback options, clear communication, and tailored user support is essential for successful adoption.
In conclusion, passkey authentication is not merely a futuristic concept—it is a practical, already-implemented solution that stands to redefine how we think about digital identity and security. As organizations and developers continue to innovate in this space, understanding both the technical and human elements of passkeys will be crucial to shaping a more secure, efficient, and user-friendly authentication landscape.
By staying attuned to the lessons learned from early adopters and the supporting best practices detailed in this analysis, businesses can prepare for a future where password-related vulnerabilities are dramatically reduced, and user satisfaction is significantly improved. The era of passkey-driven authentication is here, promising a safer and more convenient digital world.
Through this analysis, it is evident that investing in passkey technology can yield immediate security improvements while paving the way for a broader transition to a passwordless future. Embracing these advanced authentication mechanisms not only mitigates risks associated with traditional passwords but also streamlines the user experience in an increasingly interconnected digital ecosystem.
All organizations and developers are encouraged to consider these insights, evaluate their current authentication methods, and explore the integration of passkeys into their security infrastructure. The future is passwordless, and passkeys are leading the charge toward more secure, efficient, and user-centric authentication systems.
References used:
https://help.ohio.edu/TDClient/30/Portal/KB/ArticleDet?ID=1248
reddit.com/r/europrivacy/comments/16x314o/what_are_the_drawbacks_of_passkeys/
https://techcommunity.microsoft.com/blog/coreinfrastructureandsecurityblog/passkeys-authentication-across-platforms-and-devices-using-entra-id/4361075
https://medium.com/@corbado_tech/passkeys-bluetooth-cross-platform-authentication-with-qr-codes-and-bluetooth-1807265474f7
https://www.passkeycentral.org/design-guidelines/optional-patterns/cross-device-sign-in
https://www.authsignal.com/blog/articles/ux-best-practices-for-passkeys-understanding-device-initiated-authentication
https://developers.google.com/identity/passkeys



 How Mobile Technology Is Transforming Sports Betting Experiences
How Mobile Technology Is Transforming Sports Betting Experiences




